Basics Of Pentesting: Frequently Asked Questions(FAQs)
Sep 22, 2021
iCrowdMarketing powered by iCrowdNewswire
Businesses are constantly at risk for cyber attacks that can cause devastating consequences. One of the best ways to prevent these types of attacks is pentesting. Penetration testing has several advantages over other cybersecurity practices because it helps identify vulnerabilities in your network defenses. It also provides recommendations on how you can fix them. In this blog post, we will discuss what penetration testing is, why companies should have one done periodically, and any other questions someone might have about penetration testing!What is Pentesting?
Penetration testing is a security practice conducted by penetration testers or ethical hackers. Penetration tests are commonly referred to as "pen tests." Pentesting involves scanning, identifying vulnerabilities, and exploiting them to find out how serious their impact is from a business perspective.
Pentesting is conducted differently than vulnerability scans, penetration tests are dynamic. Vulnerability scans only check for known vulnerabilities. On the other hand, penetration tests will actually attack your network. So, you can see how an actual attacker would exploit these weaknesses.
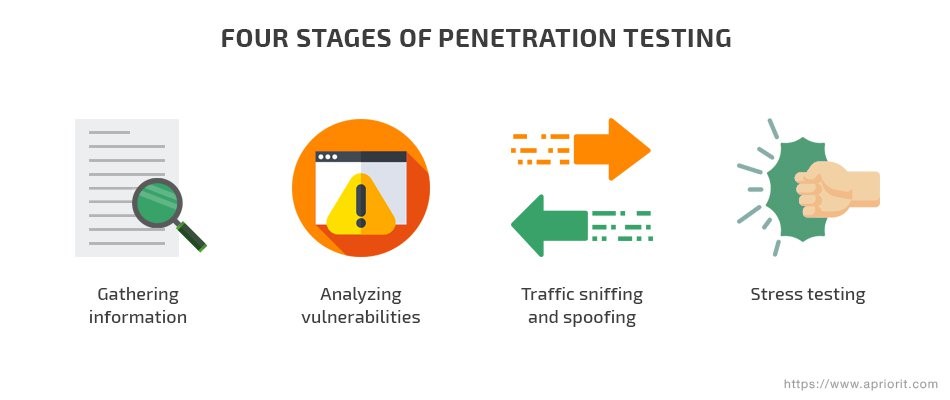
Source: Apriorit
How Does Pentesting Benefit Businesses?
Penetration tests provide the following benefits:
- Identifies security issues before malicious attackers do.
- Identifying weaknesses in your cybersecurity defenses.
- Helps you prioritize your cybersecurity efforts.
- Helps you reduce your security risks to data breaches, malware infections, and other attacks that could harm your business.
- Reduces the likelihood of a successful penetration attack against your network defenses by hackers or cybercriminals. Penetration tests can help identify multiple vulnerabilities in your system before it is beyond saving. This helps you make your company more secure.
- Helps you comply with regulations like PCI and GDPR.
- Since penetration testing simulates real-world cyber-attacks, penetration tests help you identify vulnerabilities in your network defenses and helps prioritize any mitigation efforts that should be taken.
Who Should Perform Penetration Tests?
A penetration test can actually benefit any type of company regardless of size or industry. Since penetration testers or ethical hackers conduct penetration tests, they must receive proper training and certification to determine if a company's defenses are weak and exploitable.
Pentesting is a cybersecurity practice businesses should consider performing regularly. Each industry has its own specific security needs so it's important to conduct different types of penetration tests depending on what your business does and what its goals are.
How Often to Conduct Penetration Tests?
There are several factors that influence the frequency of penetration tests. Each penetration test is different. So, it's difficult to objectively determine how often penetration tests should be performed. Some penetration tests are automated while others require manual testing. Manual testing can take longer and may need to be done less frequently than an automated penetration test or vulnerability scan.
Also, the more critical your systems are, the more important it is that they have penetration tests frequently. For example, pentesting in healthcare is much more important than pentesting for small businesses. This is because there could be serious consequences if a patient's protected health information was compromised due to weak network security defenses.
What Areas of a Company Should Be Tested?
Penetration tests can be conducted on any part or parts of your company's network/infrastructure depending on the penetration tester. Some penetration testers have different areas they usually test first, but there are several common ones that penetration testers will check for to determine if your company's network defenses are strong enough to withstand an attacker.
The most common areas penetration testers test for include:
1) Web App or Databases
Vulnerabilities in web applications or databases. Penetration tests could reveal if there is a path that someone can take advantage of by finding vulnerabilities within the system itself, not just its security configuration. Web application penetration tests are often performed by penetration testers to identify if there is a path that someone can take advantage of.
2) Demilitarized Zone
The DMZ (demilitarized zone) or "intermediate network" between the Internet and your company's internal network. Before pentesting, the tester should assess if this area will act as another layer of defense against cyberattacks.
3) Security Configurations
Weak network security configurations and vulnerabilities in operating systems. Penetration testers will check to see if there are any default passwords or other misconfigurations that could put your company at risk of a cyberattack. If you own a SaaS app, follow the linked guide for SaaS Security
In addition, penetration tests can reveal what types of encryption methods you should use for data protection as well as pentesting the physical security of your business.
Final Thoughts
Pentesting is a valuable cybersecurity practice that can help you identify and fix vulnerabilities. This process includes identifying potential attack vectors and unauthorized access methods to your systems. It will allow you to make informed decisions on what you need to do in order for your company's data assets to stay safe from the bad guys. Here are some of the key things we've covered about penetration tests so far: what they are; who should conduct one how often it should happen; where it fits into an information security program.