What is Encryption And How Does It Work?
Jul 01, 2021
iCrowdMarketing powered by iCrowdNewswire
 Encryption is a technological portmanteau, meaning a blended mix of different tech words used to describe something. In the case of encryption, the blend consists of en + crypt + tion. The ‘crypt’ part is derived from the term cryptography which is the practice and study of securing information and communication via codes, which prevents unauthorized access. So, encryption garbles stored data or data in transition into an inaccessible code locked with cryptographic technology. To ‘encrypt’ a piece or collection of data means “the process of changing electronic information or signals into a secret code (= system of letters, numbers, or symbols) that people cannot understand or use without special equipment” -a Cambridge dictionary definition of it.
Encryption is a technological portmanteau, meaning a blended mix of different tech words used to describe something. In the case of encryption, the blend consists of en + crypt + tion. The ‘crypt’ part is derived from the term cryptography which is the practice and study of securing information and communication via codes, which prevents unauthorized access. So, encryption garbles stored data or data in transition into an inaccessible code locked with cryptographic technology. To ‘encrypt’ a piece or collection of data means “the process of changing electronic information or signals into a secret code (= system of letters, numbers, or symbols) that people cannot understand or use without special equipment” -a Cambridge dictionary definition of it.Going Back in Time
Encryption has come from cryptography, which is the art, technology, or technique surrounding securing and hiding information from all eyes to see. As far as humans have existed, mysteries and codes have existed between societies. We can go back thousands of years to the roots of cryptography when Egyptian hieroglyphs were ‘ciphered’ or slightly modified to try and hide information or to send an ‘encrypted’ or secret message. On the other hand, there were also other ways like marks, seals, emblems, or logos that would personally identify a sender and the receiver would then verify this process (which effectively makes these ancient techniques the predecessors of modern signature verification). We can reach far back to 700 BC when a device called the Scytale was used that was essentially a wooden rod with ciphers (numbers, letters, or codes) on it that required a rod of identical size to be decrypted (unlocked). Over a millennium later, following this in 1467, Leon Battista Alberti had invented the first polyalphabetic ‘substitution’ cipher which contained disks containing the full alphabetical spectrum. It was just like an ancient key lock with a rotating code and an unscrambler like a keylock for a bicycle one would use today. Following this, we come to what is perhaps the most famous encryption device that arose from WWII, the ‘enigma’. It was a completely mechanical device famous for wartime encryption and has made it into popular culture and media. It allowed the Germans to send coded messages around the period of WWII and remained the most sophisticated device for that purpose for a long time after WWII.
The Computer Epoch
Now, we move into the computer epoch, or Information Age, if you will, where encryption begins. The IBM-based NSA-controlled DES or Data Encryption Standard (an early computer encryption system that utilized FIPS 46) appeared in 1977 -long before the internet was public. DES was effectively a 56-bit system (today we have upped it to 256, and more) that was deemed uncrackable, but alas was indeed broken into in the 90s. Today, the encryption process is still based around the plaintext>ciphertext>plaintext process but the way keys and bit layers are used is different and more complex.
Encryption comes in asymmetric (public key) and symmetric forms today. A symmetric process utilizes the same single key for both encryption and decryption -which is the faster method of the two. An asymmetric process requires two keys, a private and a public one. The data can only be decrypted with both keys (impossible without the private key). Encryption is used by several fundamental security protocols that are in use all over the world as standard such as TLS/SSL, IPsec, SSH, and PGP. Everything that we use daily on the internet has some form of SSL, TLS, or SSH behind it (given that it is a legitimate website or transaction). Here are the types of encryption available and in use today;
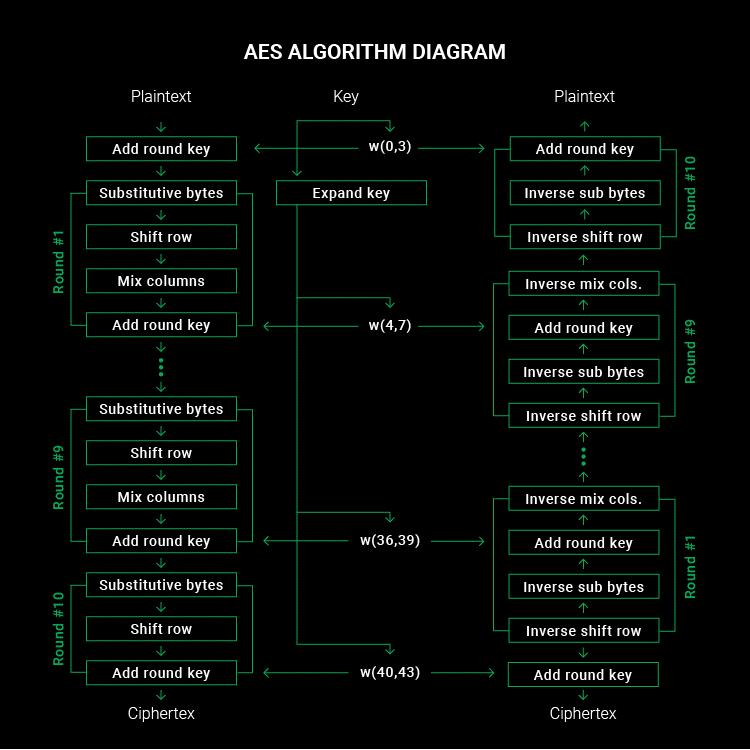
There are also ‘encryption protocols’, ‘digital certificates’, and ‘hashes’ involved in a complete encryption process but we are just looking at the specific encryption methods for now. AES and RSA (Advanced Encryption Standard and Rivest-Shamir-Adleman) are commonly used today. As far as cybersecurity is concerned, the industry recommendations for the ‘best (for lack of a better term) encryption methods are AES, 3DES, FPE, RSA, Blowfish, and Twofish. The ‘block’ sizes or encryption levels for these methods vary (128 to 256 bits), where the larger the block size the more complex the encryption and hash. Below is a diagram of a symmetric encryption process (AES) which visually describes an AES format encryption process in detail:
Why is Encryption Essential For Cybersecurity?
So we have uncovered that, without encryption, our internet and data communications would be a complete mess and impossible to manage. What we haven’t yet mentioned is the most important side-effect of having good encryption methods, that is cybersecurity (or the digital protection of systems, networks, data transmission and all data in general). Let’s list why encryption is a crucial factor in cybersecurity and how we all benefit from it;
- Transferability, meaning that encryption can be transferred between devices as well as applied to several types of devices (multi-device encryption)
- It is in line with the laws and regulations (especially in the medical industry) that state that encryption is mandatory
- Encryption works hand-in-hand with remote work (which is now standard everywhere almost) in that protecting mobile devices means protecting the company network from breaches
- Encryption standards support data integrity and increase brand reputation as well as data quality
- Encryption consolidates (strengthens) privacy and protects from data breaches
- Encryption implementation is inexpensive
- Encryption increases customer trust
Encryption is used everywhere today and stops most cybercrime before cybercriminals even have a chance to sniff out or disrupt data. For example, e-commerce (one of the largest industries in the world today) benefits from ‘session encryption’ whereas in the financial world, security for credit cards is taken care of by a process called ‘tokenization’. Nevertheless, it is a historical pattern that all encryption can be cracked at some point (like DES was in the 90s) with sufficient computing power and time. In the future, we should see the advent of quantum computing and quantum encryption, which will be a monumental step in computing. The National Academies of Sciences, Engineering, and Medicine will be convening this July to “identify potential scenarios over the next 10 to 20 years for the balance between encryption and decryption (and other data and communications protection and exploitation capabilities).” This committee is also going to assess national security and the intelligence implications of future encryption. Artificial intelligence, like Google’s neural network Google Brain is working on learning how to create and advance encryption techniques as we speak (encryption built on machine learning or ML to be precise). We may also expect ‘fully homomorphic encryption’ (FHE) that will also require enormous computing power.
Finally, Ari Juels is developing ‘honey encryption’ which offers up fake data to trick cybercriminals into thinking they have succeeded. The future of encryption is looking bright, and cybersecurity is a quickly growing industry which means that we can hope for a better, brighter IT future with much fewer cybercrime and privacy headaches. Of course, there are going to be several disadvantages of more complex encryption -that is the time, training and costs involved with the implementation of these processes. The concept of ‘going dark’ is also going to be a challenge for law enforcement, as privacy-oriented apps are on the rise (think Signal and Telegram) not to mention VPNs or Virtual Private Networks and activity on the dark web. There will be a lot of discussion surrounding encryption policy in a ‘post-quantum world, but all of that remains to be seen.
Tags: English